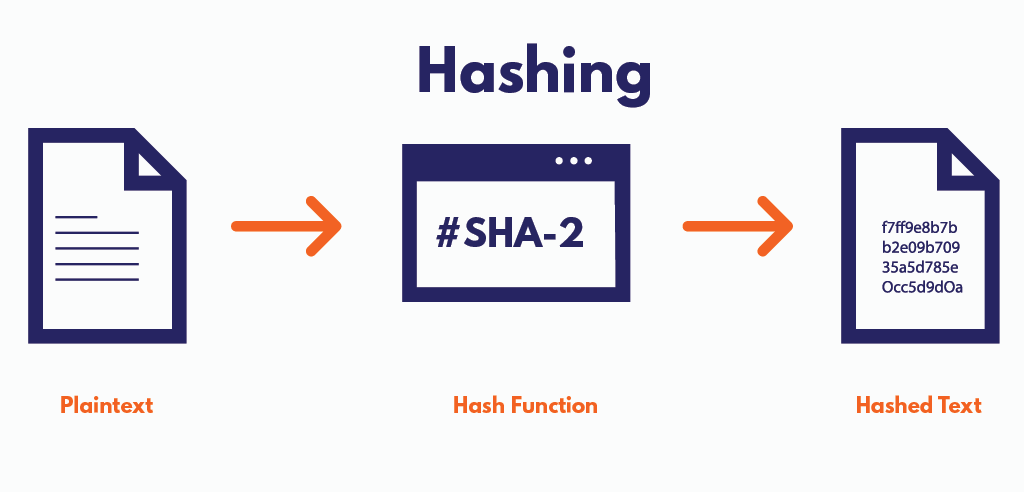
What Is a Hash?
In computer science, a hash function is a mathematical function that takes an input (or ‘message’) and produces a fixed-size string of characters, which is typically a hexadecimal number. The output is commonly referred to as a hash or hash value.
A hash function is designed to be a one-way function, meaning that it is easy to compute the hash value for a given input, but it is practically impossible to generate the original input from the hash value. This property is known as ‘collision resistance’ and is important for ensuring the security and integrity of data in various applications, including cryptography and data storage.
Hash functions are used for a wide range of applications, including digital signatures, password verification, data encryption, and data validation. In cryptocurrency, hash functions play a key role in the mining process, as miners must solve complex mathematical problems to generate new blocks in the blockchain, which are then verified using a hash function.
How Hashes Work

A hash function takes an input (or ‘message’) of any length and produces a fixed-size output, which is typically a hexadecimal number or a string of characters. The output, or hash, is deterministic, meaning that the same input always produces the same hash value.
The process of computing a hash involves several steps:
- Message pre-processing: The input message is processed to ensure that it is in a standard format and of a fixed length. This usually involves padding the message with additional bits or characters.
- Compression: The hash function applies a series of mathematical operations, such as bitwise logical operations, arithmetic operations, and modular arithmetic, to the message to compress it into a fixed-size output.
- Output: The final compressed message is output as the hash value.
Hash functions have several important properties, including:
- Determinism: Given the same input, a hash function always produces the same output.
- Collision resistance: It should be computationally infeasible to find two different input messages that produce the same hash value.
- Avalanche effect: A small change in the input message should result in a significantly different hash value.
- Non-invertibility: It should be computationally infeasible to determine the original input message from the hash value.
Hashing and Cryptocurrencies
Hashing is a cryptographic technique that is used to convert data of arbitrary size into a fixed-size output, typically called a hash or message digest. This process is one-way, meaning that it is computationally infeasible to recreate the original input data from the hash output.
Cryptocurrencies, such as Bitcoin, use hashing extensively to ensure the security of their network. In the Bitcoin network, a block of transactions is hashed using the SHA-256 algorithm, which produces a fixed-size output of 256 bits. This hash serves as a unique identifier for the block, and any tampering with the block’s contents will result in a different hash output.
Hashing also plays a key role in mining Bitcoin. Miners compete to solve a cryptographic puzzle that involves finding a hash of a block that meets a certain difficulty requirement. This process is known as proof-of-work, and it helps to secure the network by making it difficult for any individual to tamper with the blockchain’s transaction history.
Overall, hashing is a critical component of the security and functionality of cryptocurrencies like Bitcoin, and it is likely to remain an important part of these systems as they continue to evolve and mature.
What Is a Hash Function?
A hash function is a mathematical function that takes input data of arbitrary size and produces a fixed-size output called a hash value, hash code, or message digest. The output is typically a unique representation of the input data, such that any change in the input data will produce a different hash value. Hash functions are commonly used in computer science for a variety of purposes, including data integrity verification, password storage and verification, and digital signatures.
Hash functions have a number of desirable properties, including:
- Determinism: Given the same input, the hash function will always produce the same output.
- Uniqueness: Each input should have a unique hash value. However, hash functions may produce the same output for different inputs, a phenomenon known as a collision.
- Non-reversibility: It should be difficult to generate the input data from the hash value alone, without knowledge of the original input data.
- Sensitivity to input changes: A small change in the input data should produce a significant change in the hash value.
- Efficiency: Hash functions should be computationally efficient, meaning that they can generate hash values quickly and with minimal computing resources.
How Is a Hash Calculated?
A hash function takes input (also called “message”) of arbitrary size and produces a fixed-size output (often called a “hash” or “digest”). The process of calculating a hash involves the following steps:
- Preprocessing: The input message is often processed to ensure that it is a fixed length and has a uniform format. This step is important to ensure that the hash function produces consistent output for the same input.
- Partitioning: The message is partitioned into fixed-size blocks, which are then processed one at a time by the hash function.
- Compression: The hash function performs a series of mathematical operations on each block of the message, generating an intermediate hash value.
- Finalization: Once all the blocks have been processed, the intermediate hash values are combined to produce the final hash output. This step may involve additional compression and transformation steps to ensure that the final hash value meets certain security requirements, such as being resistant to collisions and preimage attacks.
What Are Hashes Used for in Blockchains?
Hashes play a crucial role in the operation of blockchains. Here are some of the main ways they are used:
- Proof of work: In many blockchains, miners compete to solve complex cryptographic puzzles to validate new transactions and add them to the blockchain. The first miner to solve the puzzle receives a reward in the form of new coins or transaction fees. Hashes are used in the puzzle-solving process as a way of verifying the miner’s work and preventing fraud. The miner must generate a hash of the block’s contents that meets a certain difficulty level. This is known as the proof of work.
- Block identification: Each block in a blockchain has a unique identifier called a hash. This hash is calculated based on the contents of the block, including the transaction data, the previous block’s hash, and a nonce (a random number used in the proof of work process). The hash serves as a unique identifier for the block and is used to ensure that the block has not been tampered with.
- Tamper-proofing: Hashes are also used to ensure that the contents of the blockchain remain tamper-proof. Any change to the contents of a block, even a small one, will result in a completely different hash. This means that if someone tries to tamper with the contents of a block, the hash of the block will change, and other nodes in the network will reject the tampered block.
- Merkle trees: A Merkle tree is a data structure that is used to efficiently verify the integrity of large amounts of data. In a blockchain, each block contains many transactions, and verifying each one individually would be time-consuming. Instead, the transactions are arranged in a Merkle tree, with each leaf node representing a transaction and each non-leaf node representing the hash of its child nodes. The root of the tree is a hash that represents the entire set of transactions in the block. This allows nodes in the network to quickly verify that a particular transaction is included in a block without having to download and verify every transaction in the block.